Silent Internal Network Segment Recon using Discovery and Broadcast Protocols
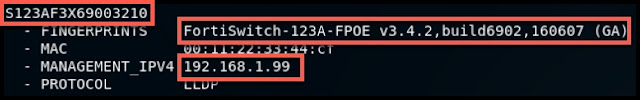
Overview - About - Affected Protocols - Obtainable Recon Data - Automating the Recon | net-recon.py - Special Thanks & Credits About In this brief post, I am going to talk about using tcpdump and PCAP files to passively collect as much recon data as possible from discovery and broadcast protocols on internal network segments. This is a method which yielded a large amount of useful reconnaissance data (which would normally be obtained via queries/scanning/some_active_or_louder_method) on my last internal engagement. We will quickly summarize affected protocols and take a look at what kind of data we can obtain. Lastly, I'll introduce my net-recon.py script, which is capable of quickly recovering and presenting correlated and normalized recon data from PCAP files. ! PSA ! - I'm not quite sure how many individuals in the InfoSec community have used this/have been using this. If this is something that many are already aware o...