Silent Internal Network Segment Recon using Discovery and Broadcast Protocols
Overview
- About
- Affected Protocols
- Obtainable Recon Data
- Automating the Recon | net-recon.py
- Special Thanks & Credits
About
In this brief post, I am going to talk about using tcpdump and PCAP files to passively collect as much recon data as possible from discovery and broadcast protocols on internal network segments. This is a method which yielded a large amount of useful reconnaissance data (which would normally be obtained via queries/scanning/some_active_or_louder_method) on my last internal engagement.
We will quickly summarize affected protocols and take a look at what kind of data we can obtain. Lastly, I'll introduce my net-recon.py script, which is capable of quickly recovering and presenting correlated and normalized recon data from PCAP files.
!PSA! - I'm not quite sure how many individuals in the InfoSec community have used this/have been using this. If this is something that many are already aware of, I apologize for reiterating old news. I just thought it was cool and provided value and decided to post about it. :)!PSA!
Recently, I started running packet captures at random intervals during the recon phase of internal network pentests (to keep a second and more detailed copy of collected data, and to troubleshoot various things that may potentially go wrong during an engagement).
Analyzing the PCAPS manually revealed a bunch of data that I did not "ask" for (this data is shown in the section after next). Initially, it was little things, such as domain and host names. After I discovered an exact Samba fingerprint within the Host Comment field of a Windows Browser Local Master Announcement, I decided to attempt to find as much data as possible from every PCAP I had collected.
I only used protocols that required no explicit connection or interaction from my host. My only requirements were that I be connected to the same internal network segment as the targets in scope, and that I'd have the ability to run tcpdump.
Affected Protocols
- Link Layer Discovery Protocol (LLDP)
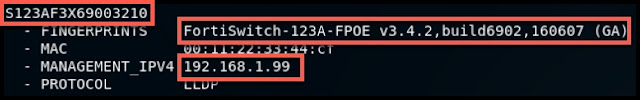
LLDP is used by network devices to advertise their identity, capabilities, and neighbors on a local network segment.
- DHCPv4 Bootstrap Protocol (BOOTP)
Used in local network segments to automatically assign IP addresses to network devices from a configuration server.
- Windows / Computer Browser Service (BROWSER)
A Microsoft Windows feature which allows users to find and browse recourses shared between local network segment neighbors.
- Multicast DNS (MDNS)
Essentially DNS used within local network segments that do not utilize local name servers.
Obtainable Recon Data without Host/System Interaction
- Switch system names, fingerprints, management IPv4 addresses
This data is obtained from network devices which utilize LLDP to make neighboring devices aware of their capabilities.
This data is obtained from network devices which utilize LLDP to make neighboring devices aware of their capabilities.
- Router, DCHP server and DNS server IPv4 addresses
This data is obtained from DHCPv4 Bootstrap Acknowledgements on the local network segment.
This data is obtained from DHCPv4 Bootstrap Acknowledgements on the local network segment.
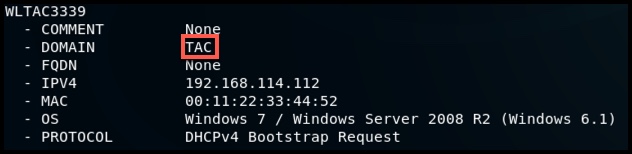
- Host names, IPv4 addresses, MAC addresses
This data can be obtained from Browser announcements and DHCPv4 Bootstrap requests.
This data can be obtained from Browser announcements and DHCPv4 Bootstrap requests.
- Domain names & FQDN's
Domain names can be obtained from DHCPv4 Bootstrap packets and Windows Browser packets, or explicitly from mDNS traffic.
FQDN's for Windows AD on local network segments can sometimes be found within DHCPv4 Bootstrap requests.
Domain names can be obtained from DHCPv4 Bootstrap packets and Windows Browser packets, or explicitly from mDNS traffic.
FQDN's for Windows AD on local network segments can sometimes be found within DHCPv4 Bootstrap requests.
- Operating System and Host Comment fingerprints
Operating system fingerprints can be found in Windows Browser packets. Host comments from Browser Local Master announcements can contain exact SMB fingerprints (Server make and semantic version).
Operating system fingerprints can be found in Windows Browser packets. Host comments from Browser Local Master announcements can contain exact SMB fingerprints (Server make and semantic version).
Automating The Recon | net-recon.py
After finding personal value in using packet captures during the start of internal network engagements (before using any other tool/method), the next step was to automate the process. As a result, I created a Python script called net-recon.py which utilizes scapy to read and scrape recon data from a PCAP file (sanitized output from net-recon.py was used for screenshots within the section prior).
The net-recon.py script is capable of parsing a PCAP for any potentially obtainable data. It's definitely a PoC at the moment and will probably break in the wild (due to minimal testing within various internal network segment / AD environments), and the code needs some cleaning up. However, it is constantly being refined, updated, and improved upon. You can find it on Github here:
If you're looking to grab secrets or credentials from a PCAP, I suggest using Dan McInerney's tool net-creds:
Integrating live network interface captures, support for additional protocols, and better correlation logic is in progress. :) Enjoy!
Special Thanks & Whats-Up!'s
- prec0re - TylerRobinson
- 0ray - grayninja
- johnhsawyer - 3nc0d3r
- cheetz - DevinErtel
- tactical_intel - dc0de
- p00r0ne - jaybeale
- haxorthematrix - j0hnny
- haxorthematrix - j0hnny
- TheBlindHacker - PermaNull
- illwill - PeterShipley
- LETHAL Security - West Coast Hackers
- ILLMOB




Comments
Post a Comment